Original: Убийство Бузины – акция устрашения НАТО
Translated by Valentina Lisitsa / Edited by @GBabeuf
Having considered some of the circumstances of the death of Oles Buzina, we are leaning towards the conclusion that his murder is one element in a bloody campaign unleashed by NATO with the aim of intimidating dissenters in Ukraine. Yet another victim of this campaign—Oleg Kalashnikov.
Judge for yourself:
The Ukrainian website “Mirotvorets” [The Peacekeeper] publishes personal information of “separatists”, “partisans of the Russian Universe” and other enemies of the Kiev regime. On April 13, 2015, a user named “404” published on this website all personal information on Oleg Kalashnikov:
https://psb4ukr.org/criminal/kalashnikov-oleg-ivanovich/ [Screenshot S1 – Translation see on bottom of page]
After the murder of Kalashnikov, the official Twitter of The Peacekeeper congratulated “Agent 404”:
https://twitter.com/psb4ukr/status/588495190115123200 [Screenshot]
“To mark the success in completing the assignment, ‘Agent 404’ is hereby awarded an extraordinary promotion, as well as a valuable gift”.
On April 14, the same user now publishes personal information on Oles Buzina.
https://psb4ukr.org/criminal/buzina-oles-alekseevich/ [Screenshot S2 – Translation see on bottom of page]
After the murder of Buzina, the official Twitter of The Peacekeeper expresses congratulations to “Agent 404”:
https://twitter.com/psb4ukr/status/588673210675232768 [Screenshot]
“Agent ‘404’ has distinguished himself again. For the successful performance of today’s assignment he is awarded a short-term vacation”.
Two coincidences is too much to consider them mere coincidences.
The website The Peacekeeper is being used as a ‘bulletin board’ for imminent death notices against those who dares to speak the truth about what is really going on in Kiev. Keep in mind that the website The Peacekeeper is actively supported by the advisor to the Interior Minister of Ukraine, the Supreme Rada deputy, Anton Gerashchenko.
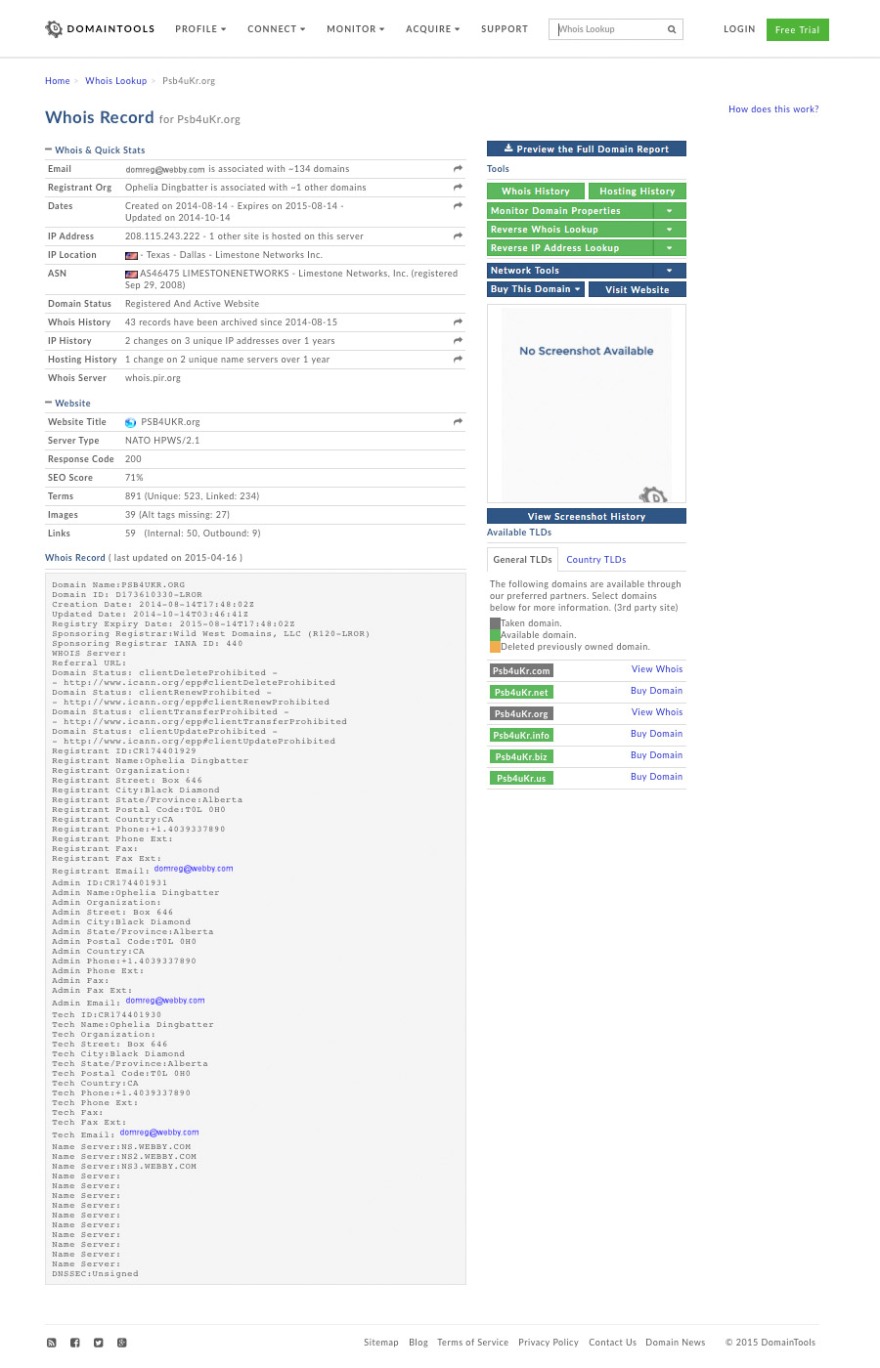
Analysing the Website https://psb4ukr.org with Domaintools.com we get following results http://whois.domaintools.com/psb4ukr.org [Screenshot]
The website is registered and located in the USA, in Texas, under the name of a Canadian national, a certain Ophelia Dingbatter. Most likely the registration name is fictitious. The only Ophelia Dingbatter found in an open search is a porn star who is hardly likely to be interested in creating websites dedicated to Ukraine.
In the table “server” the listed technical parameters state:
NATO HPWS/2.1 (a hitherto unknown type of server) http://whois.domaintools.com/psb4ukr.org
The search for other websites on the same server gives the following results:
1. operativ.info: a website that invites Ukrainians to anonymously report separatists
2. informnapalm.org: an information site with a strong anti-Russian bias
All the sites listed are hosted in the US, in Texas, most likely in the same data centre. And now—the most damning evidence:
If one were to trace the network in which The Peacekeeper is included (this can easily be done by anyone: by entering psb4ukr.org in command line in Windows) we discover that the website is located within the NATO network: domain nato.int
Here is the final destination: psb4ukr.nato.int, where nato.int is the main domain of NATO.
Due, in all likelihood, to negligence on the part of technical support, the majority of the websites used by NATO to conduct the information war against Ukraine are now exposed. At the same time, it is fair to suspect that specialists in NATO had designated Buzina and Kalashnikov as security threats to Ukraine and eliminated them, using The Peacekeeper as a tool for intimidating dissenters.
We ask you to help us spread this information, we also ask the Ministry of Foreign Affairs of Russia and the International Affairs Committee of the State Duma to take corresponding measures.
Update: We have received lots of technical input and we must elaborate on certain points.
Yes, if the administrators of The Peacekeeper wanted to create the appearance of a NATO-networked site to outside observers, they could certainly perform such a task with x amount of effort. This hypothesis, while possible from the technical viewpoint, is hardly plausible.
Several facts are known regarding the cooperation of Ukrainian power structures and NATO. The website The Peacekeeper is supported by Rada deputy Gerashchenko, an advisor to the Interior Minister, who raised funds for it and used information gathered from the website in his own speeches. He went so far as to state that “information from The Peacekeeper has been used for some time by the Interior Ministry, the Security Services of Ukraine (SBU), by the reconnaissance agencies, and by border agents for collecting information which in turn is being used for opening criminal cases and obtaining court orders for detention and arrest of separatists and terrorists.”
Thanks to the latest information leak regarding the workshop that took place in Riga on February 19, 2015, at the NATO Centre for Strategic Communications, it has become known that NATO collaborates with the Ukrainian military in the domain of information warfare and closely cooperates on certain projects on the internet http://www.ng.ru/world/2015-04-10/1_kiev.html
Political assassinations committed with the specific aim of maintaining control over countries undergoing sharp economic and political crises is the trademarked style of the USA, with many well-documented cases. A list of American death-squad hits, by no means complete, can be accessed here: http://www.serendipity.li/cia/death_squads1.htm It includes cases in countries ranging from Angola and Chile to Brazil and Thailand.
A combination of factors, and the historical and political context, indicates that a direct or proxy participation of NATO in assassinations of Oles Buzina and other Ukrainian politicians and activists is the most plausible version of events.
addendae: translation of images from The Peacekeeper files on Buzina and Kalashnikov
[Screenshot S1]
Kalashnikov, Oleg Ivanovich – added by User 404 on April 2015 – Separatist. Provocateur. Aide to militants. Maintains connections with terrorists and militants. Organised Anti-Maidan, supplied ‘titushky'[thugs for hire] – Born Nov. 6, 1962 in Rivne. Citizen of Ukraine – List of his education, employment, participation in political and civic associations – Links to various Ukrainian media sources mentioning his name – Home address.
[Screenshot S2]
Buzina Oles Alexeevich – added by User404, April 14, 2015 – Separatist, supporter of federalisation of Ukraine, writer, journalist, TV host, homophobe. Main epistolary work ‘Wurdalak [vampire] Taras Shevchenko’ – Born July 13, 1969, in Kiev. Parents of Ukrainian cossack peasant stock, father served as an officer in KGB. Great-grandfather served in Tsar’s time as army officer. During collectivisation of 1930s disenfranchised and deported to the construction of White Sea Canal – Studies : Kiev Special Secondary School #82, graduated from Kiev National University with a degree in philology and Russian Literature – Worked at several Kiev print media starting from 1993 (Kiev Vedomosti, magazines ‘Reader’s Friend’, ‘Nathalie’, ‘Ego’, ‘XXL’) – Since 2007 regularly publishes his op-eds in newspaper ‘Segodnya’ – Ran for the office of Ukraine MP from ‘Russian Bloc’ party, got 4th place with 8.22% of the votes – Served as chief editor of ‘Segodnya’ since January 2015 – In March 2015 left the newspaper in protest against censorship imposed by the newspaper owner, media company ‘Media Group Ukraine’.









Holy Shit!
Can this be true?
LikeLike
Posted by robinmorritt | Apr 17, 2015, 19:10Send it to russia-insider.com, if you haven´t already. I´m sure they´ll publish it.
LikeLiked by 1 person
Posted by Rolli | Apr 17, 2015, 19:19Reblogged this on susannapanevin.
LikeLike
Posted by susannapanevin | Apr 17, 2015, 22:40Entering whois 208.115.243.222 on a linux pc includes in the reply
Found a referral to rwhois.limestonenetworks.com:4321.
%rwhois V-1.5:003fff:00 rwhois.limestonenetworks.com (by Network Solutions, Inc. V-1.5.9.5)
network:Class-Name:network
network:ID:LSN-BLK-208.115.192.0/18
network:Auth-Area:208.115.192.0/18
network:Network-Name:LSN-208.115.192.0/18
network:IP-Network:208.115.243.192/27
network:IP-Network-Block:208.115.243.192 – 208.115.243.223
network:Organization-Name:Vladimir Kolesnikov
network:Organization-City:Velyka Oleksandrivka
network:Organization-State:OT
network:Organization-Zip:08320
network:Organization-Country:UA
network:Tech-Contact;I:abuse@limestonenetworks.com
network:Admin-Contact;I:abuse@limestonenetworks.com
network:Updated-By:admin@limestonenetworks.com
LikeLike
Posted by Keith Fernie | Apr 17, 2015, 23:57I don’t know anything about computer stuff but guess it’s safe to assume that names in the “who is” data are usually fake, right? My other questions is about the server (and I don’t even get what exactly a server is). Anyone can host a site on any server, correct? Would that mean there’s not necessarily a connection between the server owners and NATO/SBU/or even Ukrainians?
LikeLike
Posted by R_of_R (@R_of_R) | Apr 18, 2015, 02:23whois data for a domain can be faked, however it’s easily possible to have your details suppressed also. Some will still give their correct details not realising that they will be publically available. Anyone can host a site on a server they have access to. The hostname of the server can be set to a domain or subdomain which is not theirs. psb4ukr.nato.int is showing for me as a subdomain which does not exist, it may just be the hostname of the server and wishful thinking by the server owners.
LikeLike
Posted by Keith Fernie | Apr 18, 2015, 03:37A mirror webaite has been set up at psb4ukr.ninja. The whois information for this mirror shows that it has been set up by NATO CCDCOE.
LikeLike
Posted by Keith Fernie | Apr 19, 2015, 18:11What means NATO CCDCOE?
LikeLike
Posted by marcelsardo | Apr 19, 2015, 23:45https://ccdcoe.org/about-us.html
LikeLike
Posted by Keith Fernie | Apr 20, 2015, 00:28So, this is a murder for hire site OR serves as a sort of dropbox where the hitmen get their messages/orders for the next target. I think this should be sent to Sarah Wagen(something), the outspoken German Bundestag (?) member so SHE can address this in public, in Europe. Someone here must speak German and could include a note and translate it for her, if necessary. This needs to be spread ALL OVER Europe.
I’m inclined to be believe that it IS NATO behind it for the reason that in the description of Mr Buzina it said HOMOPHOBE. Last I checked, the UkieNazis are not out waving rainbow flags and carrying on about LGBT and Pussy Riot (in spite of western pressures). That’s a western/NWO agenda so using that word is a tell.
Will tweet and share on a forum but I’m a small voice. This needs spreading in many languages and around Europe.
Great find and very alarming.
LikeLike
Posted by R_of_R (@R_of_R) | Apr 18, 2015, 02:12You mean Sahra Wagenknecht. Might be worth trying…
LikeLike
Posted by babeuf79 | Apr 19, 2015, 00:23I can speak German and I would do it.
LikeLike
Posted by Klotho | Apr 20, 2015, 18:15Go Ahead. Very appreciated.
LikeLike
Posted by marcelsardo | Apr 20, 2015, 19:51Translated into Serbian: http://cirilizovano.blogspot.com/2015/04/blog-post_18.html
Поздрав, све најбоље,
Александар
LikeLiked by 1 person
Posted by Александар Јовановић | Apr 18, 2015, 04:11Хвала за превод!
LikeLike
Posted by babeuf79 | Apr 19, 2015, 00:26You should go further. You have the subdomain psb4ukr.nato.int
then look up whois of nato.int, which is:
domain: NATO.INT
organisation: North Atlantic Treaty Organization
address: Blvd Leopold III
address: 1110 Brussels
address: Brussels
address: Belgium
Otherwise, it could look like a coincident.
LikeLike
Posted by Peter | Apr 18, 2015, 07:05Reblogged this on EU: Ramshackle Empire.
LikeLike
Posted by jimsresearchnotes | Apr 18, 2015, 08:04Forget the NATO domain name. What matters is the domain itself.
Quote
The .INT domain is operated by IANA, and available for registration exclusively by intergovernmental organisations. In brief, the .int domain is used for registering organisations established by international treaties between or among national governments. Only one registration is allowed for each organisation. There is no fee for registering an .int domain name.
End Quote
So this means that site is part of a TREATY between two governments. Presumably Ukraine is one government. The question is: who is the other? The US or NATO?
Given that the US is running the Ukraine government via the US Embassy and the CIA in Ukraine, the obvious suspect is not NATO, but the CIA.
LikeLike
Posted by richardstevenhack | Apr 18, 2015, 18:24My first thought on seeing this earlier was the “Agent 404″… what is a 404 error in computing??? “file not found” . Not very clever in my opinion.
That IP address goes back to a cloud computing service in Texas called Limestone Networks. @ https://www.limestonenetworks.com/ and if you spend a few minutes on thier website you find that the servers are located at and this is exactly how they put it:
“Formally the Federal Reserve Bank of Dallas, this is the most secure data center in the central United States.
Our data center (code named DLLSTX2) is located in the heart of downtown Dallas, TX. It is in a Tier 3+ facility on the same protected power grid as Dallas 911 and the local hospitals. This means we are exempt from rolling blackouts that historically have been an occurrence due to the Texas summer heat. Power is sent to the data center from four different substations, requiring all four substations to go offline before power to the building is interrupted. Additionally, the data center is serviced by water feeds from the north and south of the building.” Oh and it just gets worse the more I read – check out the pitch to resell thier services
“You can leverage all that LSN has to offer to deliver simple, solid and superior service to your customers. Our API or premade WHMCS plugin makes it easy to offer our services under your own brand. Give the appearance of a large corporate hosting company no matter your size.” Nice way to cover NATO tracks if you had not gotten the info first. Also in Canada there’s a company called
“Commissionaires” which is a “Security Guard Service”. Once is fate, twice, is coincidence, but 10 deaths of opposition figures in recent months – I don’t even have a word for that except INTENTIONAL!!!! Watch your backs, fronts and sides everybody.
Great work exposing this!!!!!!!!!!!!!!!!!
LikeLike
Posted by silverpalomino2013 | Apr 18, 2015, 18:31By the way, the “HPWS/2.1” is almost certainly a Hewlett Packard HP-UX version of the Apache Web server. Current version is v2.32.
LikeLike
Posted by richardstevenhack | Apr 18, 2015, 18:33Reblogged this on leruscino.
LikeLike
Posted by leruscino | Apr 19, 2015, 08:04Reblogged this on Socialist Fight and commented:
the Nato murder machine:
LikeLike
Posted by socialistfight | Apr 20, 2015, 16:44Looks like someone at NATO read this article, tracert no longer returns a machine on the nato.int domain and according to domaintools the site registration was ‘Updated on 2015-04-26 ‘
LikeLike
Posted by kyle | Apr 29, 2015, 07:44Read here: http://eurazya.today/2015/04/27/nato-and-psb4ukr-org-the-link/
LikeLike
Posted by marcelsardo | Apr 29, 2015, 15:17And psb4ukr.ninja has also had an update, now using whois privacy protection, on 2015-04-28
LikeLike
Posted by Keith Fernie | Apr 29, 2015, 15:19And there’s a third one, psb4ukr.in, whois showing NATO CCDCOE
LikeLike
Posted by Keith Fernie | Apr 29, 2015, 15:57Why would a Ukrainian-run website use filenames like “nueva-imagen-de-mapa-de-bits-” for some (uploaded) images? Spanish software, or even Spanish Windows on their system?
LikeLike
Posted by radikalek | May 2, 2015, 16:27